A 10/10: CVE-2025-55182 haunting React and Next.js
CVE-2025-55182 was disclosed on December 3, and the clock was ticking. Just hours after, active exploitation attempts were observed from groups like Earth Lamia and Jackpot Panda.
I'd love to take a second and explain the distinguished terms here:
Of APTs and other Terminology
The term APT is about the abilities of the group or singular actor in question.
- Advanced (A): The actors possess a full spectrum of intelligence-gathering techniques. While they may use common tools, they can develop or access more sophisticated techniques and operate with a strong focus on operational security.
- Persistent (P): The actors have specific, long-term objectives (e.g., espionage, intellectual property theft) and maintain continuous, silent access to a network over an extended period (months or even years). They re-attempt access if lost.
- Threat (T): The actors have both the capability (skills, resources) and the intent (motivation, organization) to carry out the prolonged, targeted attack.
An APT is not always state-sponsored, the term applies to any highly skilled, well-resourced actor fitting this description.
Now, groups like Earth Lamia or Jackpot Panda are commonly referred to as China state-nexus threat groups.
Many fancy words.. what do they mean?
- State-Nexus: This means the threat group has a link or relationship (the "nexus") to the Chinese government, military (such as the PLA's Unit 61398, identified as APT1), or Ministry of State Security (MSS) intelligence services.
- Overlap with APT: Nearly all major, named China-based espionage groups (like APT41, APT40, APT10, etc.) are considered APTs because they exhibit the "Advanced," "Persistent," and "Threat" qualities.
- Distinction: The term "China state-nexus" is broader than just government employees. It often includes state-supported contractors or "patriotic hacking" groups that operate with the government's knowledge or support, sometimes blurring the lines between espionage (state-sponsored) and financial crime (like APT41, which conducts both).
Let's get back on track to the CVE at hand.
If you've never had the opportunity to work with React, I'd suggest you read some intro about it here.
Keep in mind, this is my attempt of understanding here, i am not very familiar with React, i just wanted to writeup trying to understand the issue at hand hehe.
Analyzing React2Shell (cool name, i got to admit)
Affected versions: React 19.x, Next.js 15.x / 16.x (App Router). CVSS: 10.0 (Critical)
Discovered by: Lachlan Davidson
Disclosure Date: November 29, 2025 to React, December 3, 2025 to the world
Other involved CVEs: CVE-2025-66478, Next.js's version of this
Interestingly enough, a cool aws article mentions that (fortunately), a lot of public PoCs on GitHub didn't work in reality, showing "fundamental missunderstandings of the vulnerability". A great resource for further details is, e.g., this blog article.
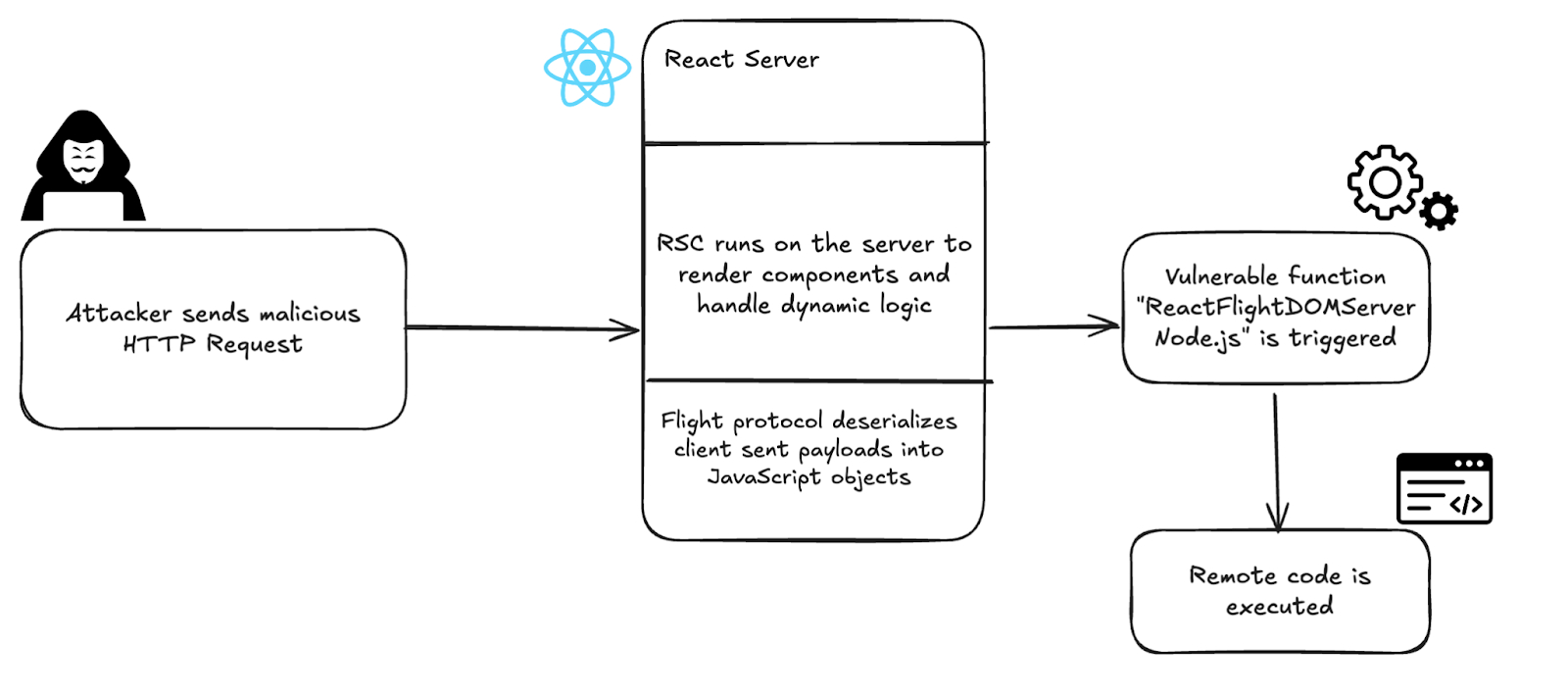
This isn't just a bug; it's a fundamental flaw in how the new React Server Components (RSC) architecture talks to itself.
The Ecosystem: Flight Protocol
RSC relies on the Flight Protocol to stream data and UI components from the server to the client. It’s the glue that holds modern React apps together. The vulnerability lies in how the server reads (deserializes) this protocol.
The Exploit: "The Thenable Trap"
As Lachlan Davidson’s PoC demonstrates, the exploit abuses the special $@ syntax used in Flight to reference "Chunks" (data pending on the server).
The core issue is Unsafe Deserialization via a "Thenable" object. In JavaScript, if an object has a .then() method, the runtime treats it like a Promise and automatically tries to "resolve" it by executing that function.
As far as I've understood the main PoC from Mr. Davidson:
The Attack Flow:
- The Bait: The attacker sends a malicious JSON object (mimicking a Promise) via a
multipart/form-datastream. - The Trigger: The React server deserializes the object, sees the
.thenproperty, and, trying to be helpful, executes it. - The Hook: The attacker points
.thento an internal React gadget (like_responseor_formData). - The Shell: This forces the server to re-enter its parser with a malicious context, allowing the attacker to chain internal calls and execute
child_process, granting a shell.
// CONCEPTUAL PAYLOAD (Simplified)
{
"maliciousChunk": {
"$$typeof": { "$": "react.element" }, // 1. Look like a React Element
"then": {
"$": "@12345" // 2. The Trap: Point 'then' to an internal RCE gadget
}
}
}This attack is particularly dangerous because it is unauthenticated and works on default configurations of frameworks like Next.js (App Router) that use React Server Components.
Outro: The Consequences
We need to talk about the fallout such a desastrous vulnerability can create.
1. The "Fake PoC" Noise As noted by AWS and others, many public PoCs are "fake." They try to call child_process directly. This fails because the vulnerability requires a specific gadget chain (internal React functions) to reach the system shell. Don't trust every GitHub repo you see; verify the chain.
2. The Trust Deficit React Server Components (RSC) were already controversial due to their complexity. A CVSS 10.0 RCE in the default configuration of the world's most popular web framework (Next.js) will slow adoption.
What You Must Do
- Patch: Upgrade to React 19.0.1+ and Next.js 15.0.5+ / 16.0.7+ immediately.
- Audit: Check your logs for requests containing
$@or unusualmultipart/form-datastructures sent to your Server Action endpoints. - WAF: Ensure your WAF is blocking the specific Flight Protocol signatures associated with this exploit.
React2Shell proves that as we move logic from the Client to the Server, we might bring the Server's vulnerabilities (RCE) along for the ride.
No spam, no sharing to third party. Only you and me.






Member discussion